When using Ansible to manage Foreman with the Foreman Ansible Modules, we need to provide a username and a password for authentication. But what happens if the user doesn’t have a password in Foreman, because external authentication (like LDAP or Kerberos) is used?
In the case of LDAP we still can provide the LDAP password to Ansible, and things will work.
However, providing the LDAP password to Ansible also means that Ansible is now in the possession of a credential that can be used in other contexts than Foreman, which is something nobody really wants to do.
Some LDAP servers even require a kind of 2FA authentication, by requiring the password to be transferred as <password><token> and thus the transferred password changes on each request.
Enter “Personal Access Tokens” (PAT)! Foreman supports Personal Access Tokens since 1.17 and allows the use of PATs instead of the password when performing API requests. As Personal Access Tokens are stored and validated by Foreman, they can be used regardless of the requirements and constraints the “real” authentication method enforces.
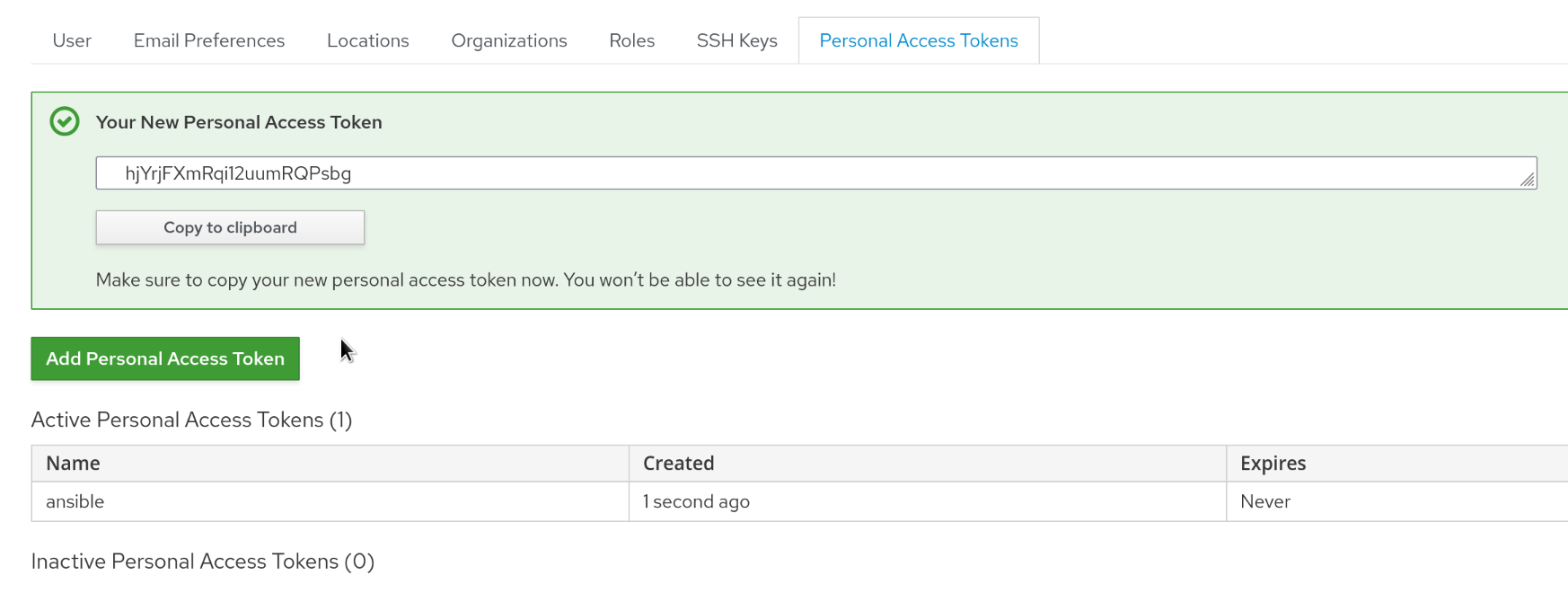
To create a Personal Access Token, we go to the user’s profile
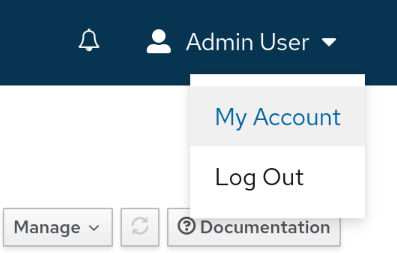
Select the “Personal Access Tokens” tab
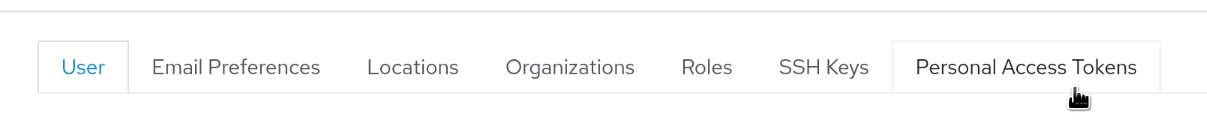
Click “Add Personal Access Token”
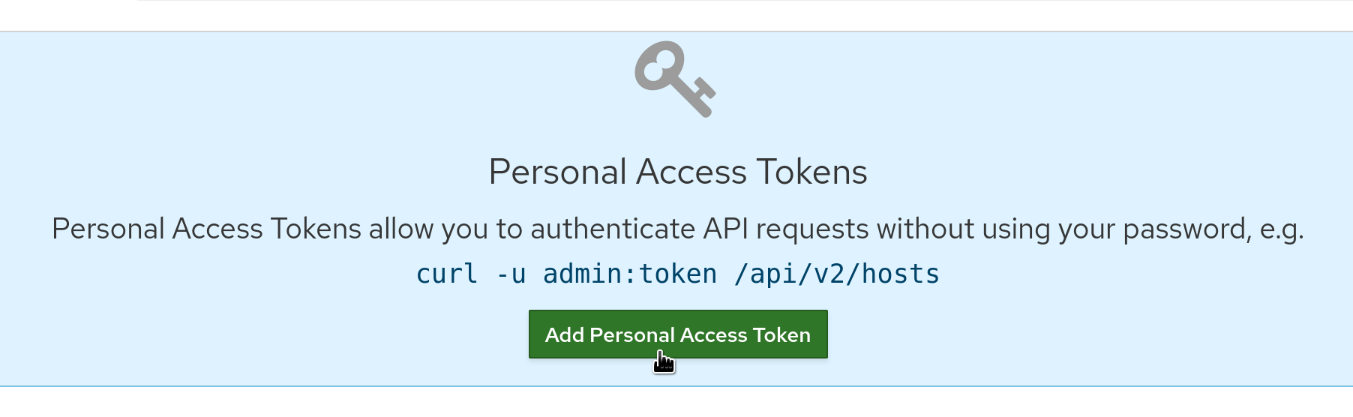
Fill out the form, the name is something that the token can be later be identified by, say “ansible” and the expiration date is optional
Once the form is submitted, the newly created token is shown and can be used
Now the token can be used as the password in any Ansible playbook:
---
- hosts: localhost
tasks:
- name: set instance title
theforeman.foreman.setting:
server_url: https://foreman.example.com/
username: admin
password: hjYrjFXmRqi12uumRQPsbg
name: instance_title
value: the awesome and secure instance